ATP Gov’s 2025 Tech Trends: Navigating the Future with Zero-Trust

Written by Eric Montersarelli
In the ever-evolving cybersecurity landscape, Zero Trust (ZTA) has Trust as a cornerstone for protecting sensitive information and critical infrastructure.
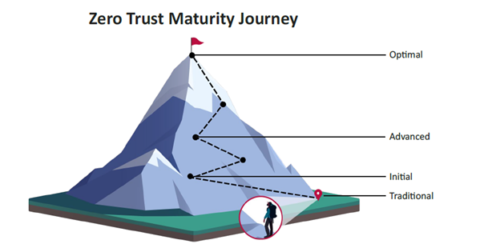
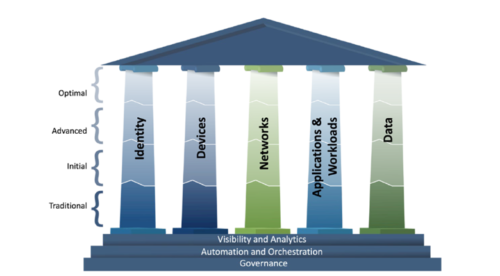
Unlike conventional IT security approaches that assume Trust within the trust boundaries, Zero Trust assumes that threats can exist inside and outside the network. ZTA requires continuous verification of every access request, ensuring only authenticated and authorized users and devices can access resources. It goes beyond the current limits of RoBAC (Roles Based Access Control) and “Need to Know” systems using a form of RuBAC (Rules Based Access Controls).
Compared to the commercial sectors, the federal government faces unique cybersecurity challenges, increasing threats from sophisticated cyber-attacks and data breaches. Implementing a zero trust architectures is crucial for mitigating these risks and safeguarding national security.

U.S. Executive Order 14028 (Improving the Nation’s Cybersecurity) underscores the importance of adopting ZTA principles across federal agencies. These principles enhance security posture by minimizing the attack surface, preventing unauthorized access, and ensuring robust protection of sensitive data.
By continuously validating credentials and employing stringent access controls, ZTA reduces the risk of breaches and ensures a secure environment for critical operations. This proactive stance against potential threats aligns seamlessly with federal mandates and helps agencies stay ahead of adversaries in an ever-evolving cyber landscape.
As we navigate the future, Zero Trust will continue to play a vital role in ensuring the security and resilience of government projects.

Our commitment to Zero Trust for 2025 and beyond
As government projects become increasingly reliant on digital infrastructure, the need for robust cybersecurity measures becomes paramount. Zero Trust is not just trusted but necessary for future-proofing sensitive data, government projects, and military missions. Zero Trust represents a fundamental shift in how we approach cybersecurity. At ATP Gov, we are proud to be at the forefront of this transformation, working with our OEM partners to deliver innovative solutions that protect our nation’s most critical assets.
Our extensive network of OEM partners, including industry leaders like zScaler, Fortinet, Broadcom, CISCO, CyberArk, and Dynatrace, enables us to deliver interoperable packages and solutions that fit your needs. These partnerships allow us to offer advanced identity-based access controls, real-time monitoring, and encryption capabilities, ensuring our clients have the best tools to implement zero trust effectively in their enterprise.
At ATP Gov, we provide cutting-edge product packages and toolsets designed to satisfy the various pillars of ZTA, including solutions tailored to meet the needs of federal agencies. Stay tuned for more insights in our 2025 Tech Trends series as we explore the technologies shaping the future of federal cybersecurity.
Images used in this article sourced from CISA Zero Trust Maturity Model Version 2.508c


